Big 3 on the Information Superhighway
July 17th, 2009 — Scott HartleyWith the resignation of Obama Car Czar Steven Rattner, the Big 3 –Ford, General Motors, and Chrysler– are reeling, and attention has again focused on automotive management of Federal bailout money. E.M. Forster’s Internet “screens with a view,” could provide insights on strategic, regional brand and inventory decisions.
Within the Big 3, brand management and differentiation remains challenging. However, Google Insights for Search indicates relative strengths, direction and amplitude of trending, and geographic hotbeds. At Ford Motor Company, Lincoln has more than double the search volume as Mercury, and three times that of Volvo. But while Mercury has interest in Kansas, Oregon, and California, Volvo is predominately popular in Massachusetts, New Hampshire, and Rhode Island. In fact, seven of the top ten “Volvo” query states are in New England.
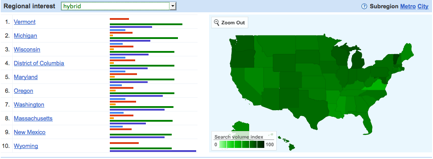
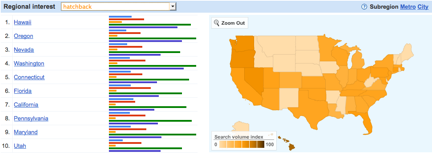
Comparing common models such as Sedan, SUV, Hatchback, Hybrid, and Pickup, managers would discover relative consumer preferences, and see that online interest –arguably a leading indicator of consumer engagement– is highly regional. Over the past 90-days, American Google search volume on “Hybrid” cars is 265 percent greater than “Sedan,” and 900 percent greater than search on “Hatchback” vehicles. But automotive managers would also realize that consumers in the Northeast are are increasingly interested in Hybrid vehicles, while Hatchbacks have strong popularity in Hawaii and the Pacific Northwest. Despite rising oil prices, online queries about Sport Utility Vehicles (SUV) remain highly popular across the Southern United States, from Texas to Florida.
With SUV online popularity strong in Southern states, Ford executives might compare search volumes across their line of relevant vehicles, namely the Expedition, Explorer, Escape, and Edge. While the Ford Expedition and Edge have comparable interest, there is 60 percent greater search volume on the Escape, and 140 percent on Ford Explorer. However, the Ford Expedition’s limited Internet traffic comes from the region with the strongest ties to Sport Utility Vehicles. Despite the Explorer’s popularity in Alaska, the Escape’s popularity in Michigan, and the Edge’s popularity in Iowa, the Expedition’s most interested consumers hail from Louisiana, Texas, and Florida. By understanding regional interests in vehicle type, Ford could better target appropriate vehicles regionally.
As Steven Rattner makes a return to Cerberus Capital –on the shores of the Hudson, if not the River Styx– his replacement would be apt to consult Internet search as a leading indicator of consumer behavior. The Big 3 may yet become reliant on Gore’s Information Superhighway as much as they have on Eisenhower’s Interstate Highway.





 Click Here
Click Here