Civilization is a draft. Provisional. Scaffolded. Under construction. For example:

That’s Thomas Jefferson‘s rough draft of the Declaration of Independence. The Declaration hasn’t changed since July 4, 1776, but the Constitution built on it has been amended thirty-three times, so far. The thirteenth of those abolished slavery, at the close of the Civil War, seventy-seven years after the Constitution was ratified.
Today we are in another struggle for equality, this time on the Net. As Brian Grimmer put it to me, “Digital emancipation is the struggle of the century.”
There is an ironic distance between those first two words: digital and emancipation. The digital world by itself is free. Its boundaries are those of binary math: ones and zeroes. Connecting that world is a network designed to put no restrictions on personal (or any) power, while reducing nearly to zero the functional distance between everybody and everything. Costs too. Meanwhile, most of what we experience on the Net takes place on the World Wide Web, which is not the Net but a layer on top of it. The Web is built on architectural framework called client-server. Within that framework, browsers are clients, and sites are servers. So the relationship looks like this:
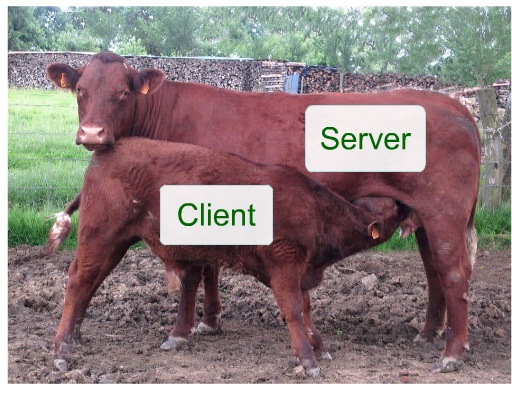
In other words, client-server is calf-cow. (I was once told that “client-server” was chosen because “it sounded better than ‘slave-master.’” If anyone has the facts on that, let us know.)
Bruce Schneier gives us another metapor for this asymmetry:
It’s a feudal world out there.
Some of us have pledged our allegiance to Google: We have Gmail accounts, we use Google Calendar and Google Docs, and we have Android phones. Others have pledged allegiance to Apple: We have Macintosh laptops, iPhones, and iPads; and we let iCloud automatically synchronize and back up everything. Still others of us let Microsoft do it all. Or we buy our music and e-books from Amazon, which keeps records of what we own and allows downloading to a Kindle, computer, or phone. Some of us have pretty much abandoned e-mail altogether … for Facebook.
These vendors are becoming our feudal lords, and we are becoming their vassals.
It’s handy being a vassal. For example, you get to use these shortcuts into websites that require logins:

To see how much personal data you risk spilling when you click on the Facebook one, visit iSharedWhat (by Joe Andrieu) for a test run. That spilled data can be used in many ways, including surveillance. The Direct Marketing Association tells us the purpose of surveillance is to give you a better “internet experience” through “interest-based advertising—ads that are intended for you, based on what you do online.” The DMA also provides tools for you to manage experiences of what they call “your ads,” by clicking on this tiny image here:
![]()
It appears in the corners of ads from companies in the DMA’s AdChoice program. Here is one:

The “AdChoices” text appears when you mouse over the icon. When I click on it, I get this:

Like most companies’ privacy policies, Scottrade’s says this: “Scottrade reserves the right to make changes to this Online Privacy Policy at any time.” But never mind that. Instead look at the links that follow. One of those leads to Opt Out From Behavioral Advertising By Participating Companies (BETA). There you can selectively opt out of advertising by dozens of companies. (There are hundreds of those, however. Most don’t allow opting out.)
I suppose that’s kind of them; but for you and me it’s a lot easier just to block all ads and tracking on our own, with a browser extension or add-on. This is why Adblock Plus tops Firefox’s browser add-ons list, which includes many other similar products as well. (The latest is Privacy Badger, from the EFF, which Don Marti visits here.)
Good as they are, ad and tracking blockers are still just prophylactics. They make captivity more bearable, but they don’t emancipate us. For that we need are first person technologies: ways to engage as equals on the open Net, including the feudal Web.
One way to start is by agreeing about how we respect each other. The Respect Trust Framework, for example, is a constitution of sorts, “designed to be self-reinforcing through use of a peer-to-peer reputation system.” Every person and company agreeing to the framework is a peer. Here are the five principles to which all members agree:
| Promise | We will respect each other’s digital boundaries |
Every Member promises to respect the right of every other Member to control the Member Information they share within the network and the communications they receive within the network. |
| Permission | We will negotiate with each other in good faith |
As part of this promise, every Member agrees that all sharing of Member Information and sending of communications will be by permission, and to be honest and direct about the purpose(s) for which permission is sought. |
| Protection | We will protect the identity and data entrusted to us |
As part of this promise, every Member agrees to provide reasonable protection for the privacy and security of Member Information shared with that Member. |
| Portability | We will support other Members’ freedom of movement |
As part of this promise, every Member agrees that if it hosts Member Information on behalf of another Member, the right to possess, access, control, and share the hosted information, including the right to move it to another host, belongs to the hosted Member. |
| Proof | We will reasonably cooperate for the good of all Members |
As part of this promise, every Member agrees to share the reputation metadata necessary for the health of the network, including feedback about compliance with this trust framework, and to not engage in any practices intended to game or subvert the reputation system. |
The Respect Network has gathered several dozen founding partners in a common effort to leverage the Respect Trust Framework into common use, and within it a market for VRM and services that help out. I’m involved with two of those partners: The Searls Group (my own consultancy, for which Respect Network is a client) and Customer Commons (in which I am a board member).
This summer Respect Network launched a crowd-funding campaign to get this new social login button rolling:

It’s called the Respect Connect button, and it embodies all the principles above; but especially the first one: We will respect each others’ digital boundaries. This makes itthe first safe social login button.
Think of the Respect Connect button project as a barn raising. There are lots of planks (and skills) you can bring, but the main ones will be your =names (“equals names”). These are sovereign identifiers you own and manage for yourself — unlike, say, your Twitter @ handle, which Twitter owns. (Organizations — companies, associations, governments — have +names and things have *names.)
Mine is =Doc.
Selling =names are CSPs: Cloud Service Providers. There are five so far (based, respectively, in Las Vegas, Vienna, London, New York/Jerusalem and Perth):
Here’s a key feature: they are substituable. You can port your =name from one to the other as easily as you port your phone number from one company to another. (In fact the company that does this in the background for both your =name and your phone number is Neustar, another Respect Network partner.)
You can also self-host your own personal cloud.
I just got back from a world tour of places where much scaffolding work is going up around this and many other ways customers and companies can respect each other and grow markets. I’ll be reporting more on all of it in coming posts. Meanwhile, enjoy some photos.





Leave a Reply