In 2006, an AT&T engineer named Mark Klein revealed a secret room inside a major Internet hub that was only accessible to engineers with NSA security clearance. His revelation was written up in the New York Times as part of its larger coverage of NSA wiretapping of domestic communications. Among the documents revealed by Klein was an equipment list for the secret room. Among a dozen high powered servers and networking devices on the list was a single device by a company called Narus.
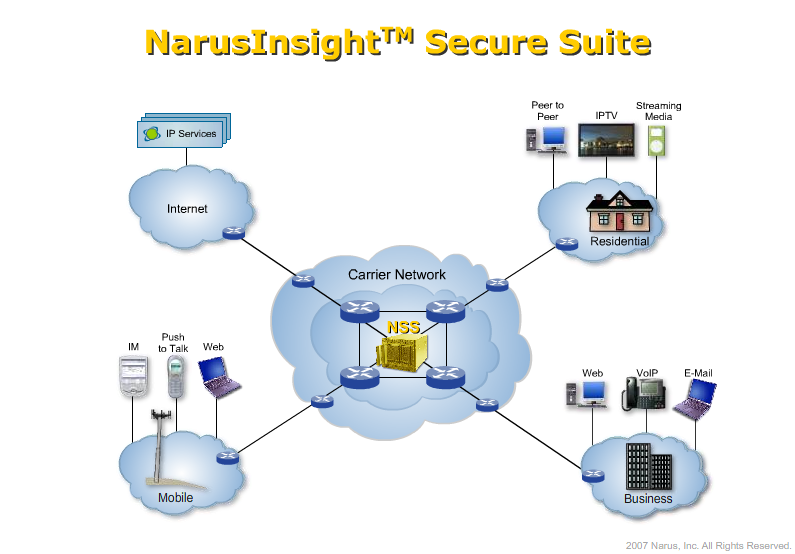
Narus describes itself as “the leader in real-time traffic intelligence for the protection and management of large IP networks.” In practice, Narus produces network monitoring software for two purposes: protection and management of the traffic itself and “semantic analysis” of the traffic. The first product sits in the middle of large network carriers (like AT&T) and provides analysis of traffic to detect cyber-security threats like worms, denial of service attacks, and network hijackings. Here’s a diagram from a Narus demo showing its network management product:
The second “semantic analysis” product is marketed to governments for use in law enforcement:
* Intercept and surveillance application for real-time precision targeting of any type of IP traffic
* Provides real-time, surgically precise targeting, allowing full IP session reconstruction and visibility for targeted traffic such as webmail, e-mail, IM, chat, Voip and other IP-based communications
* Enables the capture of packet-level, flow-level and application-level usage information for forensic analysis, surveillance and regulatory compliance
* Secures network monitoring with the complete capture of only targeted data
* Insight into, and monitoring of, the entire network regardless of size, speed or the routing topology of the network
In other words, Narus sells the “mass intercept” black boxes that sit in phone company closets surveilling customer traffic for the NSA and other intelligence / law enforcement agencies. The Narus box listed in the document revealed by Klein was one of the Narus products designed for this use.
Both of the Narus products are built on the same underlying platform, because the task of surveilling a network to manage it and surveilling a network to process user traffic is largely the same. Indeed, the two blend into one another, as promoted by Narus:
The same product that can block worms and DDoS attacks can also block “rogue VoIP” connections in Pakistan, “mediate” dangerous websites in Saudi Arabia, and “tier” service for preferred content providers. And a slightly differently focused version of that same product can collect, sort, and archive user content, including web, email, chat, and even webmail for targeted or mass surveillance. Once a box with these sorts of specific surveillance capabilities is sitting in the middle of the network, it potentially has access to all of the data flowing over that network. It’s a natural marriage for the company who makes the boxes to extend into both the network management and the government surveillance markets, and in the spaces between.
The common theme through these uses is security through surveillance. Narus’ network management features provide security from botnets, worms, and other such cyber threats by surveilling massive amounts of traffic for “actionable intelligence” on the state of the network. Narus’ mass intercept features provide security from terrorists and dissidents by surveilling massive amounts of traffic for “actionable intelligence” on the communications of users within the network. Many scholars argue that that judging surveillance as a tradeoff between security and liberty make no sense: massive use of CCTV cameras in the U.K. has not been shown to decrease crime and domestic surveillance of domestic phone calls in the U.S. by the NSA has led to lots of investigations of pizza places. But the utility of Narus and other such systems seems both straightforward and necessary in the age of 40Gbs DDoS attacks.
The danger of this confluence of functions is that Narus boxes are given complete access to “over 30% of the world’s Internet traffic and meeting the most stringest requirements of the world’s largest networks such as at&t, KT, KDDI, Telecom Egypt, KPN and US Cellular.” The use of the boxes both places trust in the systems that Narus is building but also makes their more intrusive uses simply a matter of flipping a switch.
{ 1 } Trackback
[…] Narus: Security through Surveillance […]